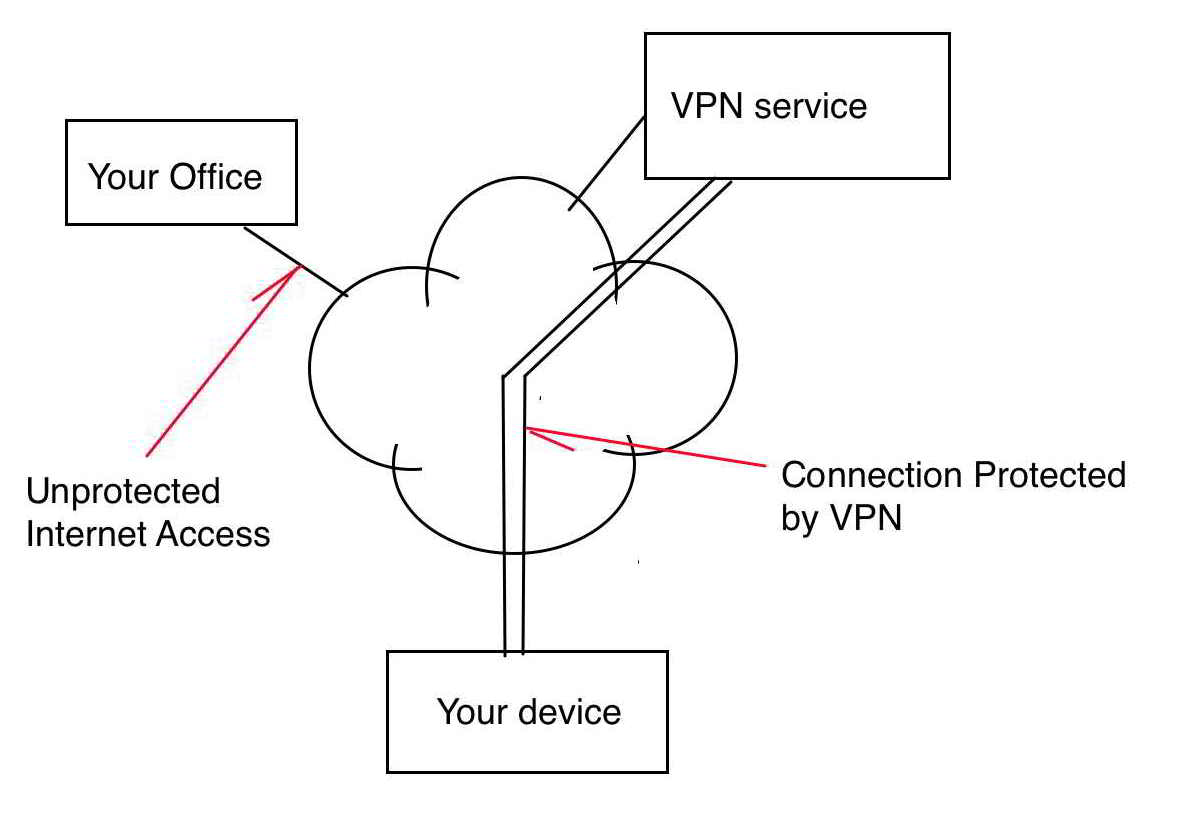
Using a public VPN service, your connection is only partly safe
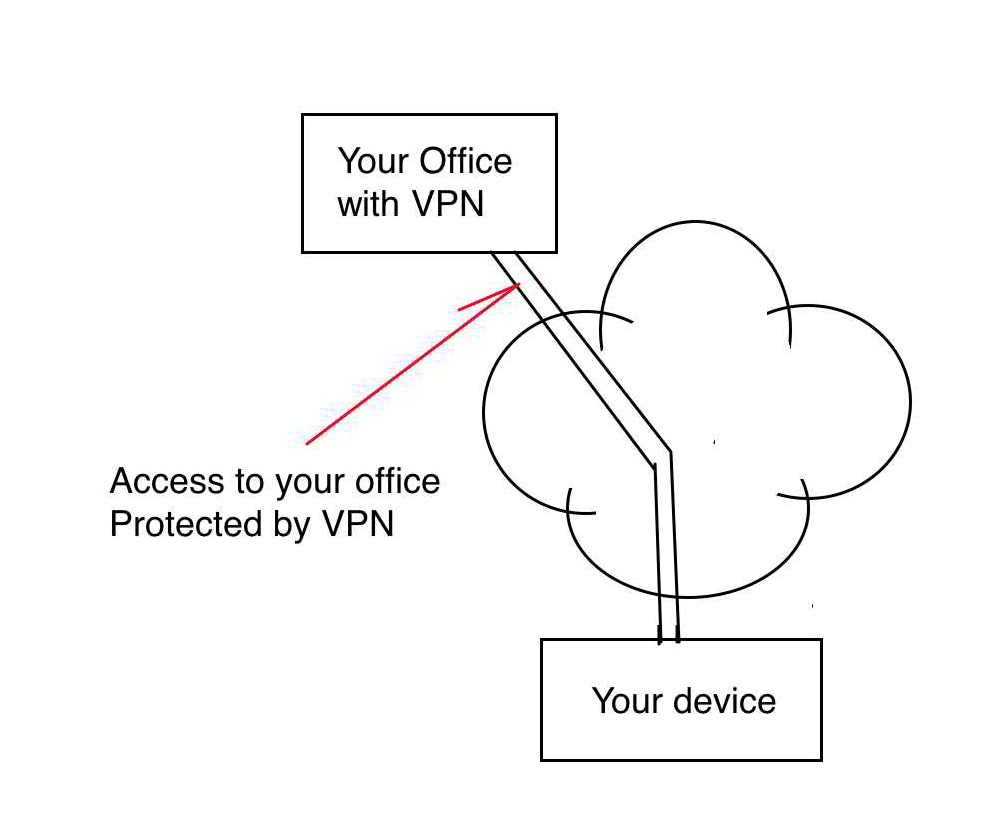
Using your own VPN, your connection is safe all the way to and including your office
The C19 virus has forced many organisations in to remote working. This raises a number of security issues for example taking work (members data) home.
GDPR is clear that this is not the thing to do also such data will need to be shared between other workers at remote locations also some third party systems require a known WAN IP for their access.
The answer, keep all the data in the office where it is reasonably secure and access it securely from many locations.
This is like being in the office without physically being there. There is also an interesting bonus. If your home worker only has a slow broadband, it doesn't matter as once connected to the office all actions through the remote office computer will be at the office internet speed. The office broadband should be fibre.
There is also the need for remote system monitoring of the office broadband, server and even power. The office is your central hub and should it have a power cut, broadband fail or a hacking attempt all your access could or will fail.
|
1 |
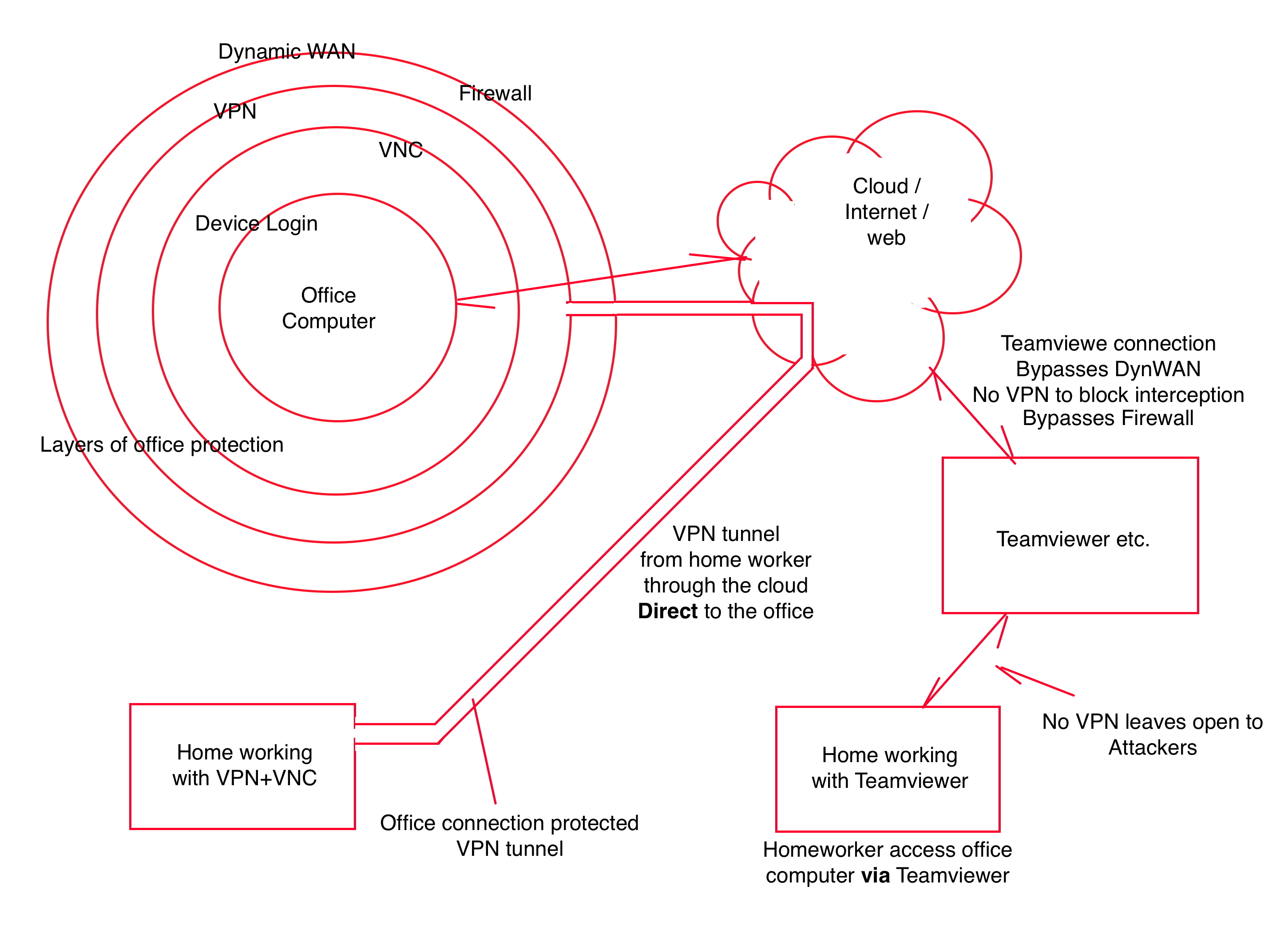
Dynamic office WAN IP The use of a dynamic WAN IP helps to prevent DoS attacks and router probing of the office network, remember no one is going to be there to notice any problems. |
|
2 |
VPN Server Allows remote access to the office LAN through a VPN, this should include SSL as part of its connection and is essential for security from remote user to the office. |
|
3 |
SecureDNS The use of a secure DNS acts to block access to undesirable websites and helps stop spyware, ransomware etc. |
|
4 |
VNC Remote access to individual computers is via VNC. The is an industry standard for remote access which is included in modern OS's or is a free download for older systems. |
|
5 |
VPN Client VPN client is used to access a remote static IP service. Some older security systems use static IP as a form of CLI to allow access to their systems. This allows us to keep our dynamic WAN IP protection. |
|
6 |
Multi -factor authentication (mfa) adds more layers of security to your accounts. Verifying your identity using another factor (like your phone or other mobile device) prevents anyone but you from logging in, even if they know your password. |
Why Common VPN products do not do the job:
Although NordVPN and other such services can give protection to your local wireless connection they are not suited to protecting your office.
The protection they supply is between your computer and their service, it is not end to end.
Having your own VPN protects your connection from your computer to your office, from end to end.
The connection stages to your office are:
|
Stage 1 |
VPN to office VPN Server |
Username and password |
|
Stage 2 |
VNC to individual computer |
device address and Password |
|
Stage 3 |
Login to that individual computer |
Password |
|
|
Using a public VPN service, your connection is only partly safe
|
|
|
Using your own VPN, your connection is safe all the way to and including your office |
VPN Remote Access Client configuration
The main reason to use the OpenVPN protocol is because it's very secure, really stable, and it works on multiple platforms. It can also be found built in to many routers. Most security experts recommend always using OpenVPN for anything you do online – especially since it's such a transparent option (due to it being open-source).
Installing VPN on Client computer.
Download OpenVPN connect free from: https://openvpn.net/vpn-client/
|
|
|
|
|
|
|
|
|
VNC needs to be configured to connect to individual computers. VNC comes pre-installed on many modern systems as part of the operating system. If you need to install VNC it can be downloaded from : |
|
By default, TeamViewer isn’t a particularly secure application. It favours ease of use over difficult-to-navigate security procedures.
The way TeamViewer, Google remote, etc. work are by having an application run on an individual computer which 'talks' to the TeamViewer server. This server acts like a mirror and reflects the office computers details to any user logged in to it by running TeamViewer on a remote computer.
This is fine but because the individual computer connects directly with the TeamViewer server, the connection comes from the wrong side of the network i.e. is an outgoing connection, therefore:
|
1 |
The information is not protected by a VPN tunnel. |
|
2 |
Bypasses the office network firewall. |
|
3 |
Bypasses hiding from the web with a dynamic WAN. |
|
4 |
Not a direct connection but via the services server giving more chances for interception. |
|
5 |
The only challenges are the TeamViewer code and the computers login. |
|
6 |
Not a private service, these well known services are targeted by hackers. |
|
|
As recent as December 2017 TeamViewer was found to have a security issue TeamViewer issues emergency fix for desktop access vulnerability |
This
is ok if you are watching someone remotely connecting to the computer
but not recommended for unattended use.
 How
It Works
How
It Works
|
1 |
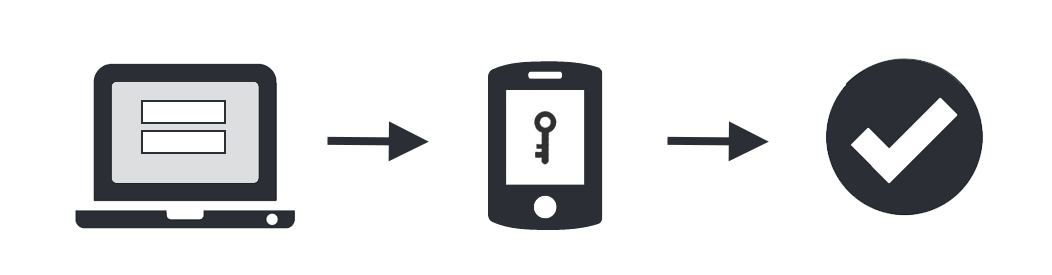
Enter username and password as usual |
|
2 |
Use your phone to verify your identity |
|
3 |
Securely logged in |
You'll login as usual with your username and password, and then use your device to verify that it's you. Your device can do this via SMS, voice call, one-time passcode, the Mobile smartphone app, and so on.
No mobile phone? You can also use a landline or tablet, or a hardware token. With MFA you can link multiple devices to your account, so you can use your mobile phone and a landline, a landline and a hardware token, two different mobile devices, etc. this is where mfa is different to 2fa
Why Do you Need This?
Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked — you might not even know someone is accessing your account.
Multi-factor authentication adds another layer of security, keeping your account secure even if your password is compromised. With Push notifications, you'll be alerted (on your phone) as soon as someone tries to log in.
|
|
Examples of MFA
Below: a Banking PIN Sentry |
|
|
Above: Smart phone app.
Below: Bypass code
|
|
Above: Authentication QA code |
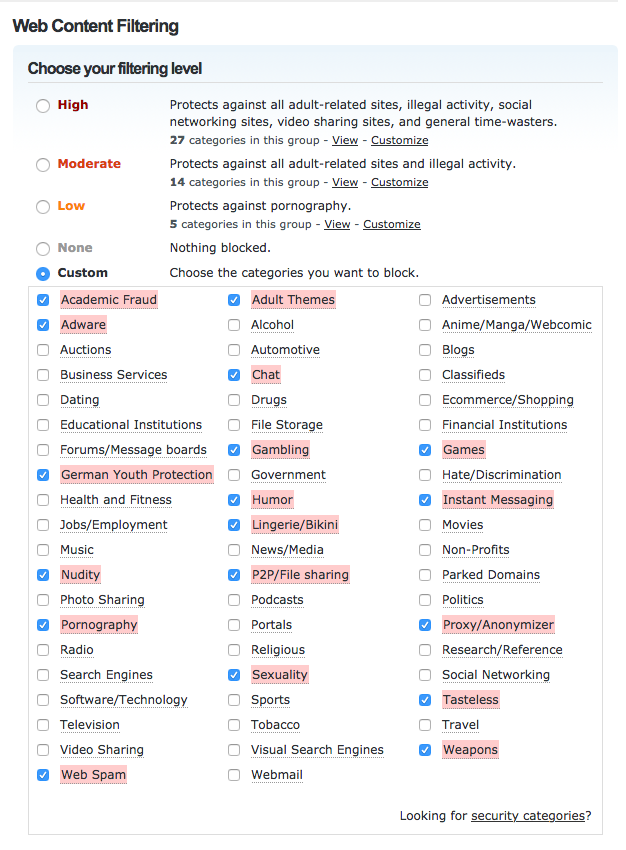
An example using Cisco umbrella's OpenDNS
Delivers faster, more reliable internet
Thanks to openDNS global data centres and peering partnerships, they shorten the routes between every network and their data centres–making our internet access even faster.
Helps make the web a safer place with filtering or pre-configured protection. Cisco safeguard against inappropriate content and more.
It’s the easiest way to add content filtering controls to every device on your network Protect users everywhere with DNS layer security OpenDNS a fast, secure, and reliable internet experience to over 24,000+ organisations.
It uses the internet’s infrastructure to block malicious and unwanted domains, IP addresses included dark web, and cloud applications before a connection is even established.
|
||
|
This report shows occasional spikes in slowness which is in keeping with normal working.
Weekly email monitoring reports on any blacklisting that might occur, usually due to email spoofing. |
||
|
|
Backup is to a remote 'personal cloud' device.
|
1 |
Keep physical control of data (GDPR)
|
|
2 |
If need to relocate, (no access to current office) personal cloud device can be moved to the new location and restore preformed using LAN without need of broadband.
|
|
3 |
Personal cloud device can be moved to other locations making it always available, even during holidays. Some adjustment of the local router may be needed (port forwarding) |
|
|
|
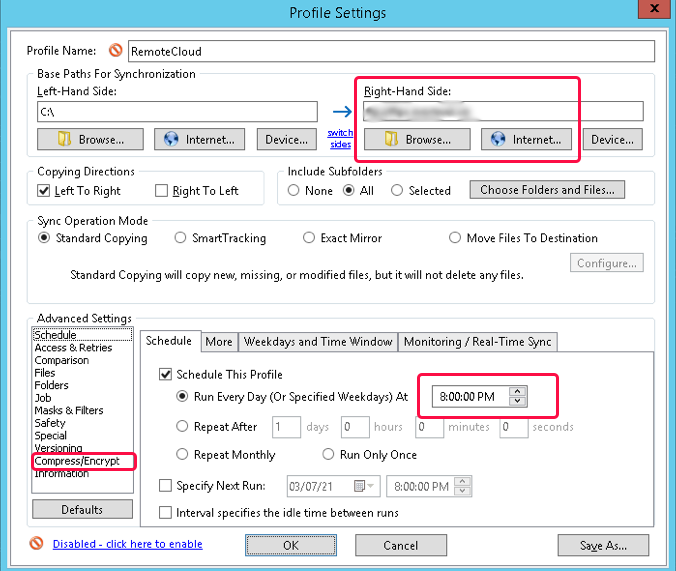
Items to note:
|
1 |
Backup is to a remote cloud device |
|
2 |
Backup starts at 8:00 pm so will not impact on the working day |
|
3 |
data is compressed and encrypted before being transferred |
|
4 |
Backup software supports versioning so previous backups can be accessed. |
Print to locations remote from the office is achieve through Cloud printing using the PrinterShare cloud printing service.
http://www.printershare.com/download-macos.sdf
This is the service of choice because:
|
1 |
Independent service |
|
|
2 |
Ability to encrypt documents |
|
|
3 |
Account activity and use controlled by administrators |
|
|
4 |
After 31 December 2020, Google Cloud Print is no longer supported. |
|
|
|
|
|
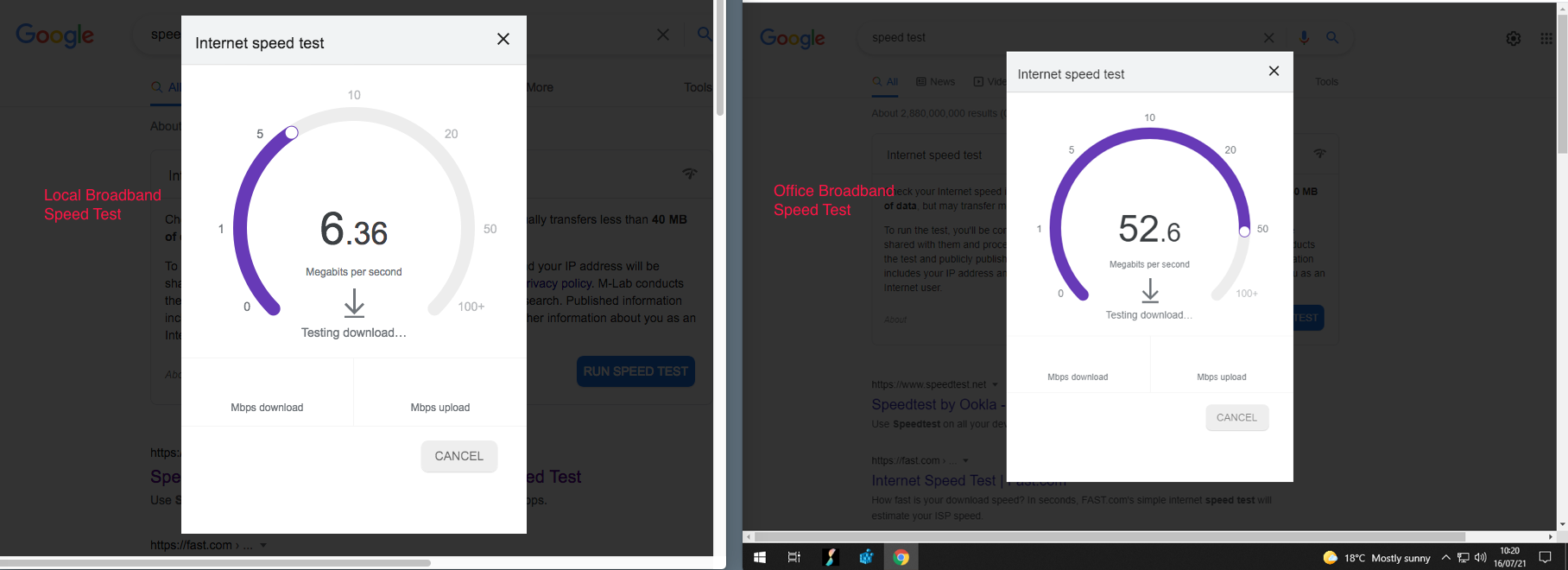
An example of speed increase. The home workers broadband in this example is 6Mb but access via the office computer uses the office fibre at 52Mb
Incoming numbers
|
|
Main Number |
Ring Group |
|
|
Members Number+ out of hours |
IVR |
|
Extension |
Location |
Network Address |
|
210 |
office Reception |
192.168.*.* |
|
211 |
Loans |
192.168.*.* |
|
212 |
Front Desk |
192.168.*.* |
|
215 |
Credit control |
192.168.*.* |
|
216 |
Cordless |
N/A |
|
217 |
Remote worker |
10.0.0.10 |
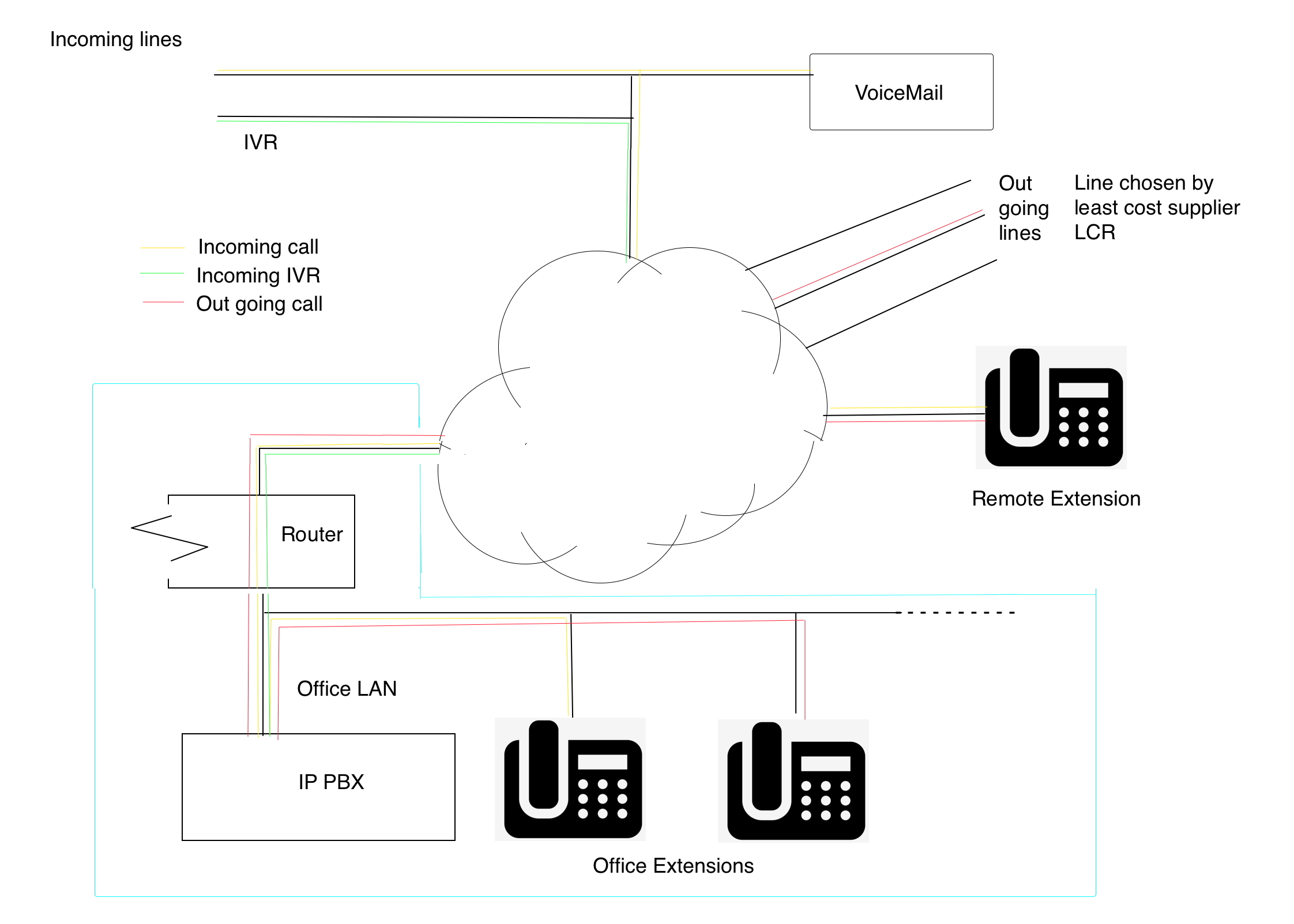
Internet based phone system. Showing remote extension, cloud voicemail, multiple incoming lines, multiple out going lines with multiple suppliers for best costs.
Things to note:
|
1 |
Voicemail is part of the incoming lines so if your office has a power cut or a broadband fault you won't loose any calls. |
|
2 |
The use of your own PABX gives you all the functions, cloud based systems usually charge extra for each function (IVR, Call recording, etc.) some even charge for incoming calls. |
|
3 |
IP phone systems are targeted. Ensure you have some system of limiting misuse. Knowing your approx monthly cost and using a top up system is a good way to limit risk. |

|
Smart phone App for use with phone system downloadable from: This free app can support texting, video and conference calls |